Paperkey is a command line program for Linux that allows you to export your GPG private key in a human-readable format. It works by removing the redundant parts of a private key and leaving only its critical secret bits.
This article will guide you through the process of installing and setting up paperkey on Ubuntu, and show you how to store your paperkey backup as a QR code and extract it during recovery.
Why Use Paperkey to Backup Your GPG Key
One of the biggest advantages of paperkey is that its format is often smaller than a regular PGP private key block. This makes it easier to manage and store in a variety of formats. For example, a paperkey backup is small enough that you can write it on a piece of paper.
As such, paperkey provides you with the opportunity to remove your PGP private key from any electronic device. While some devices today provide stellar “data at rest” encryption, keeping your data offline is still a reliable way to make your key inaccessible to bad actors.
Tip: learn how you can easily encrypt files inside the Linux terminal using Tomb.
Obtaining and Installing Paperkey
- The first step in installing paperkey is to update your entire system. This will ensure that your system’s repository information has the correct package information for paperkey.
sudo apt update sudo apt upgrade
- Run the following command to install the paperkey application:
sudo apt install paperkey
- Check whether paperkey was properly installed in your system:
paperkey --version
Configuring Your Paperkey Backup
With paperkey installed, you can start backing up your GPG secret key. For this guide, I am going to back up a 4096-bit RSA/RSA key that I made by running gpg --full-gen-key.
- To start, list all the available keys in your GPG keyring:
gpg --list-keys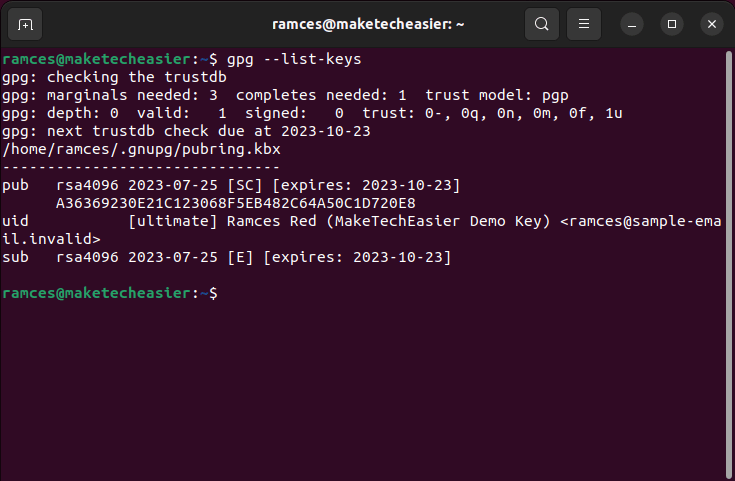
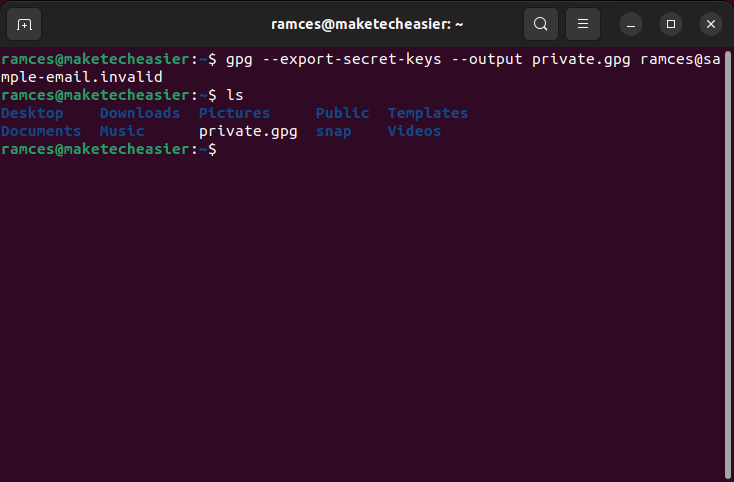
- Output a binary copy of the private key that you want to export:
gpg --export-secret-keys --output private.gpg your-gpg@email.address
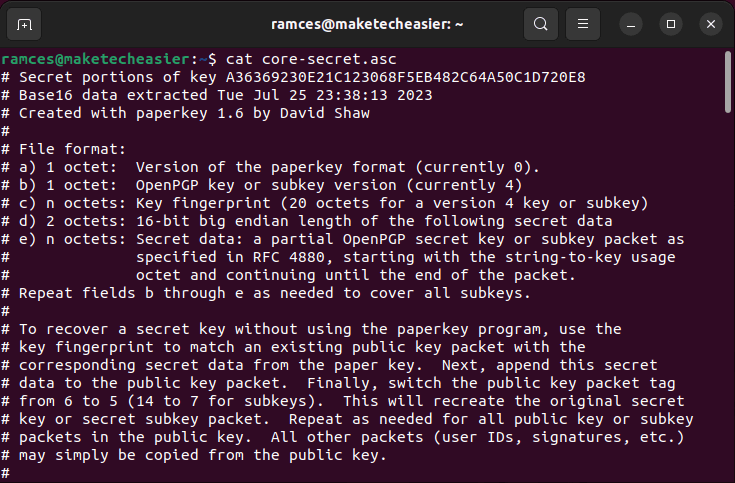
- Run paperkey along with your .gpg file to extract its core secret key in a plain text file:
paperkey --secret-key private.gpg --output core-secret.asc
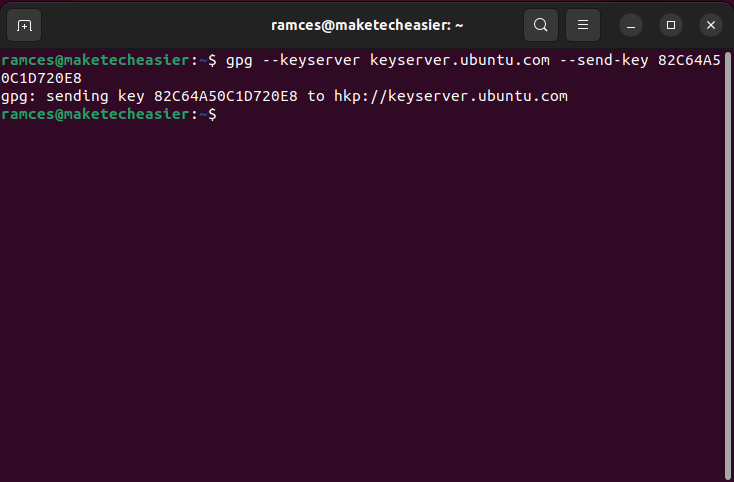
- Upload your public key to a well-known keyserver. This will ensure that you will be able to reconstruct your key during the recovery process:
gpg --keyserver keyserver.ubuntu.com --send-key YOUR-KEY-FINGERPRINT
Note: You can find your GPG key’s fingerprint by running gpg --with-colons --list-keys your-gpg@email.address | grep pub | awk 'BEGIN{FS=":"} {print $5}'.
- After that, completely erase your private key file:
shred -uvn 10 ./private.gpg
Tip: Shred is not the only tool that you can use to irreversibly remove files. Learn the best tools that you can use to securely delete files in Linux.
Converting Your Paperkey to QR Code
Aside from exporting in a text file, you can also use paperkey to convert your secret to a machine-readable format. For example, you can use basic UNIX pipes to redirect your core secret to a QR code generator. This makes it easier to recover your secret in a reliable and error-proof way.
- Install the
qrencodeprogram from your package manager:
sudo apt install qrencode
- Export your GPG private key in a binary format:
gpg --export-secret-key --output qr-private.gpg your-gpg@email.address
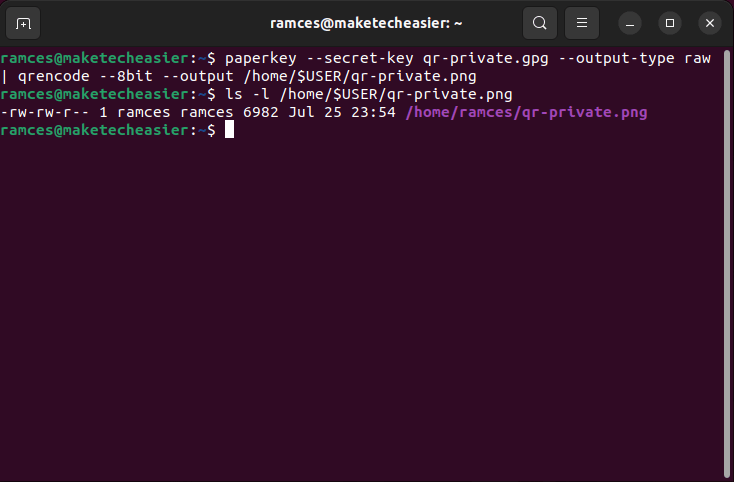
- Run paperkey using your “qr-private.gpg” file and redirect its output straight to qrencode:
paperkey --secret-key qr-private.gpg --output-type raw | qrencode --8bit --output /home/$USER/qr-private.png
- Open your system’s file manager and check for the QR image.
Restoring Your Paperkey Backup
At this point, you have a proper paperkey backup of your GPG private key. You can either write the human-readable text file or print the QR code on a piece of paper and store it somewhere safe.
To recover your GPG key:
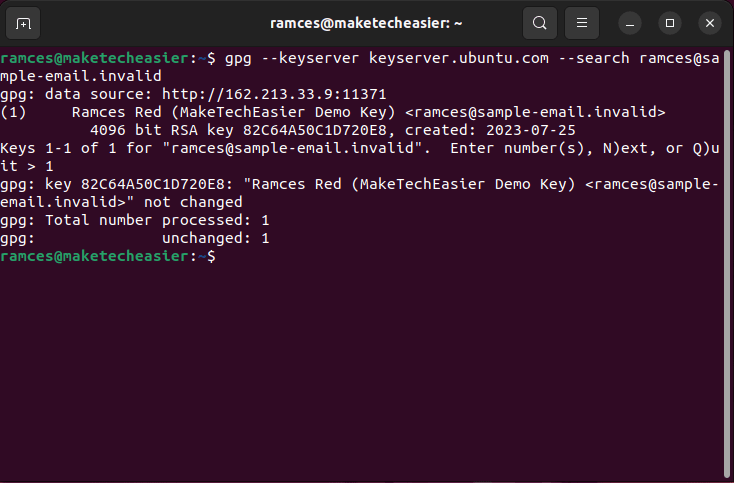
- Search for your public key on the keyserver that you sent it to:
gpg --keyserver keyserver.ubuntu.com --search your-gpg@email.address
- Select the key that you want to retrieve from the search results list.
- Export your public key to a binary format:
gpg --export --output public.gpg your-gpg@email.address
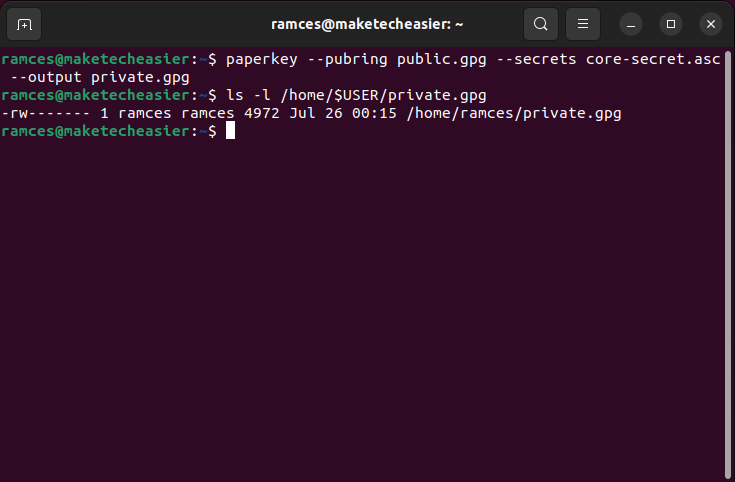
- Reconstruct your original private key by using both the
--pubringand--secretsflags in paperkey:
paperkey --pubring public.gpg --secrets core-secret.asc --output private.gpg
- Import your newly reconstructed secret key using GPG:
gpg --import ./private.gpg
Restoring a Paperkey Backup from a QR Code
You can also retrieve your GPG private key by combining a paperkey QR image with an existing GPG public key for your identity.
- Install the zbar utility to enable QR and barcode scanning on your computer:
sudo apt install zbarcam-gtk zbar-tools
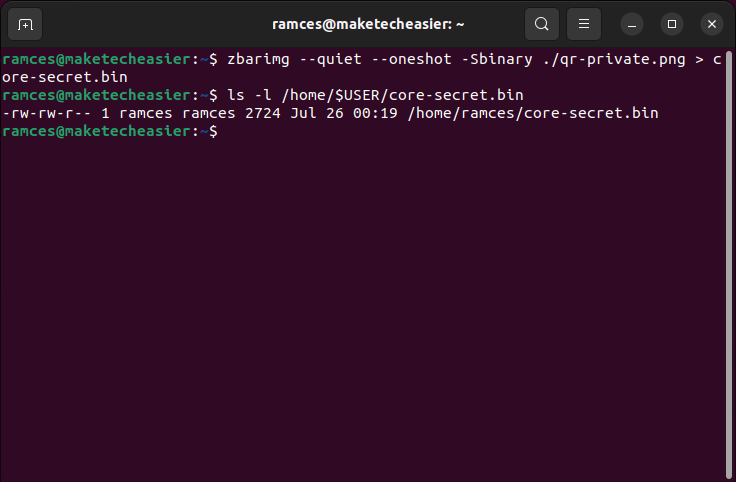
- Decode your QR image using zbarimg and pipe its output to a file:
zbarimg --quiet --raw --oneshot -Sbinary ./qr-private.png > core-secret.bin
- Reconstruct your original GPG private key using paperkey:
paperkey --pubring public.gpg --secrets core-secret.asc --output private.gpg
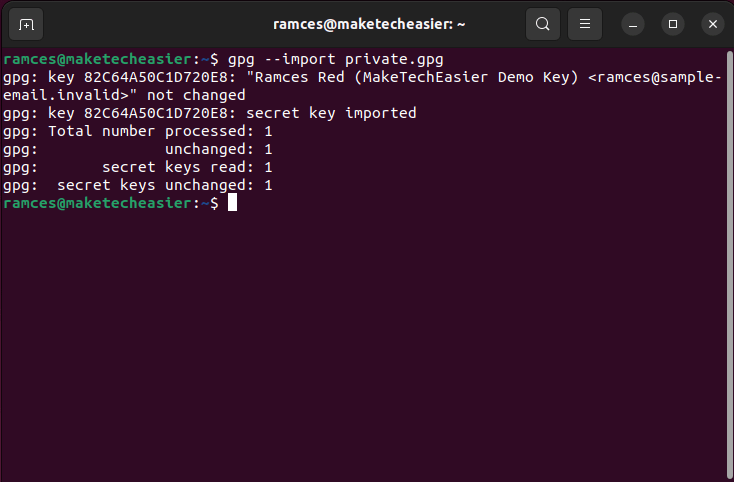
- Import your private key to your GPG keyring:
gpg --import ./private.gpg
Good to know: Learn how you can create secure backups by creating an encrypted cloud drive using rclone.
Frequently Asked Questions
Is a Paperkey backup secure?
A paperkey backup, by default, does not modify any of the inherent properties of your GPG key. This means that it will only be as secure as its encryption key and the number of bits that it is using.
One of the advantages of paperkey is that it does not rely on electronic devices in order to store private key data. This can provide a great deal of security especially if you are using a networked computer that other users can access online.
I am getting a corrupted input error when I backup my GPG private key.
This issue happens whenever paperkey reads a file with an incorrect data type. The most common cause for this incorrect data type is an ASCII-armored GPG private key. To fix this, you need to remove the --armor option from your GPG export command.
Is it possible to convert my paperkey to a different image format?
Since paperkey only provides raw binary data, it is possible to use different image generation programs to create your own “paperkey backup image.”
For example, you can install GNU barcode and run: paperkey --secret-key qr-private.gpg --output-type raw | barcode -S > private.svg to create an SVG barcode of your core secret file.
Image credit: Sincerely Media via Unsplash. All alterations and screenshots by Ramces Red.
Our latest tutorials delivered straight to your inbox